The Globalization of cybercrime
A Holistic view of Cyber Security and Cyber Crime
“Listcrime is the community that helps you spot scams before you fall for them with AI-powered tools and real reports from people like you.”
Download the App or Login through our Portal and join us.

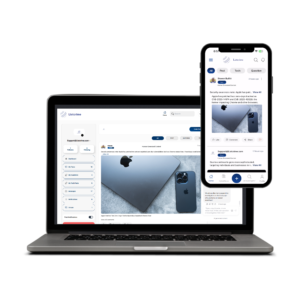
About listcrime
Listcrime is both a cybersecurity platform and a powerful suite of investigation tools. It unites everyday users and cybersecurity experts to fight cybercrime through community knowledge, real-time alerts, and intelligent verification tools.
The platform also enables direct engagement with current and former federal, state, and local law enforcement professionals, allowing users to ask questions, share experiences, and receive informed guidance grounded in real-world investigative and operational expertise.
Listcrime supports both anonymous public participation and verified professional collaboration, with capabilities varying by trust tier.
- The Listcrime AI Investigator™ instantly analyzes scams, fraud attempts, and digital threats using global intelligence and OSINT data.
- Manual Lookup Tools provide fast verification for texts, emails, URLs, domains, limited phone numbers, and businesses.
- The Listcrime Community Platform allows users to post, share, and collaborate in private or public groups dedicated entirely to cybersecurity—bringing victims, professionals, and investigators together in one trusted environment to strengthen awareness, prevention, and collective defense against cybercrime.
DOWNLOAD THE APP HERE:

Protection: “Before you click that link, check it on Listcrime.”
Community: “Join the movement that’s fighting cybercrime together.”
Empowerment: “Listcrime gives you the tools law enforcement uses.”

 Web Portal Login
Web Portal Login
For law enforcement, retail investigators, bank fraud teams, and financial institutions, the AI Investigator serves as a force-multiplier—automating time-consuming early-stage checks, consolidating open-source and threat intelligence, and providing fast, contextual insights that support informed investigative decisions. The platform does not collect evidence, interfere with legal processes, or replace existing investigative tools. Instead, it helps professionals prioritize leads, reduce friction, and focus their expertise where it matters most.
For everyday citizens, ListCrime provides a simple way to verify and validate suspicious phone numbers, emails, websites, domains, and business entities encountered in daily life. The goal is early awareness, education, and prevention—helping users make safer decisions before harm occurs.
“Listcrime supports both anonymous public participation and verified professional collaboration. Capabilities vary by trust tier.”
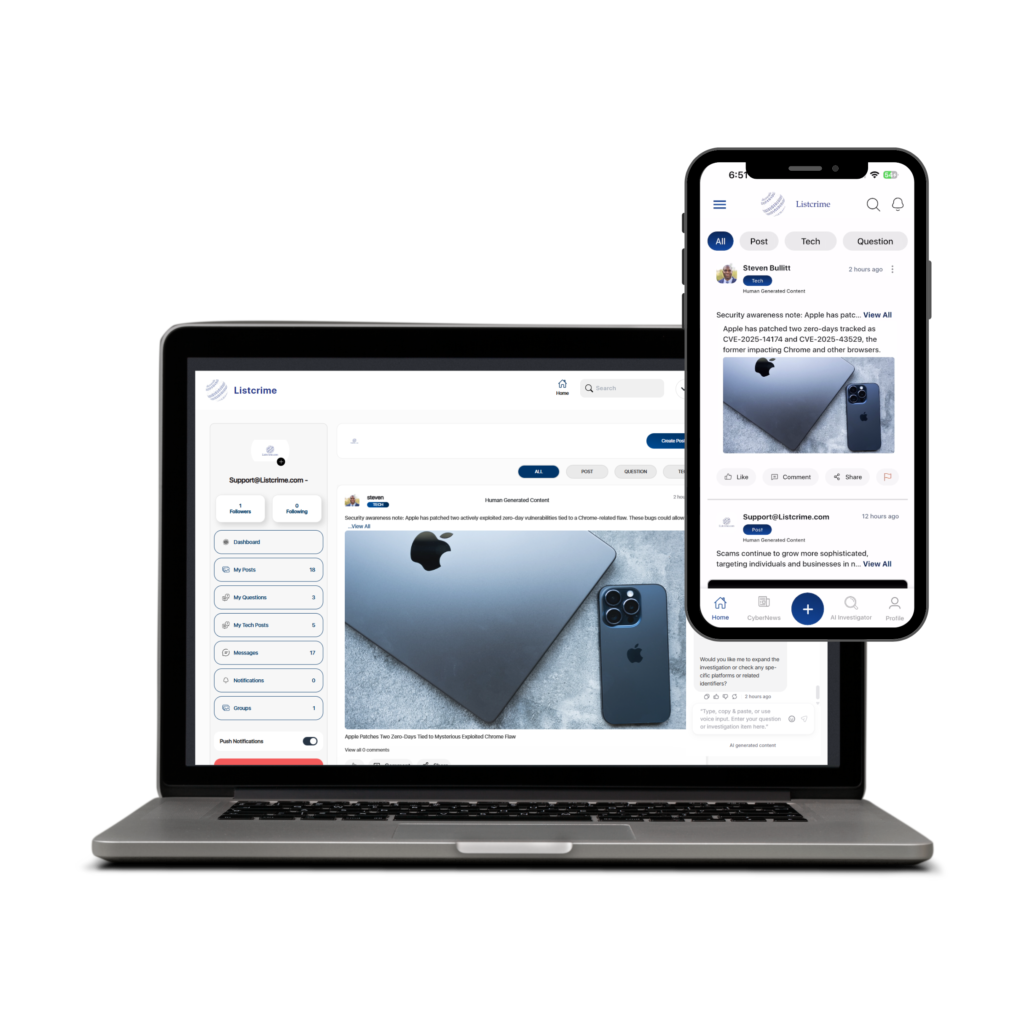
WELCOME TO LISTCRIME
-
Listcrime is your trusted resource for navigating the complexities of cybercrime. Our mission is to protect high-risk demographic users including the unbanked, elderly, and mobile generation by equipping them with the knowledge and tools needed to prevent cyber threats and take decisive action if they become victims. We are committed to empowering individuals and businesses with cutting-edge solutions to combat fraud, scams, and online exploitation.
WHY LISTCRME IS NEEDED
Today’s cyber ecosystem is more complex than ever—shaped by global technology growth, AI, and a decentralized digital world. Listcrime.com provides a secure space for both experts and everyday users to share insights, discuss threats, and report incidents. By building a community of vigilance, Listcrime helps reduce cyber risks and strengthen online safety for everyone.
Your own personal AI Investigator
 Web Portal Login
Web Portal Login
A Borderless Solution
Cybercrime has no borders, and Listcrime is built to match that reality—connecting people worldwide to share verified intelligence and stop threats before they spread.
AI Investigator: Instantly check URLs, domains, businesses, job ads, texts, and emails in real time. Your personal AI agent analyzes threats on the spot so you can protect yourself and alert others.
See the Whole Picture
Listcrime unites everyday users and cyber experts, giving you the tools to verify suspicious messages, report scams, and stay protected—together.
AI Investigator: Use the AI Investigator to scan suspicious links, phone numbers, domains, or messages in seconds. Get immediate intelligence so you know what’s safe and what’s a scam.