The Ten (10) essential Layers to addressing Cyber Crime and Cyber Security
The Challenges of Internet Protocol Resources, Layer 1
Layer 1 Addresses the challenges we face within the cyber ecosystem. Our Ecosystem is built with complexities, due to technological advances, globalization, international laws, and a host of other issues that are only magnified by a decentralized digital ecosphere. Internet innovation, digital transformation and the exponential growth of technology all contribute to the complexities of the Cyber Ecosystem of Internet Protocol Resources.The Stakeholders of Internet Protocol Resources, Layer 2
Layer 2 (The DNS Layer) is a decentralized international multi-stakeholder network of autonomous groups responsible for the management and distribution of Internet number resources such as Internet Protocol (IP) addresses and Autonomous System Numbers (ASNs). There are a wide range of stakeholders involved in the management of IP Resources from civil society, to academia, business, and more, who work together for the public good. SEE ICANN IMAGE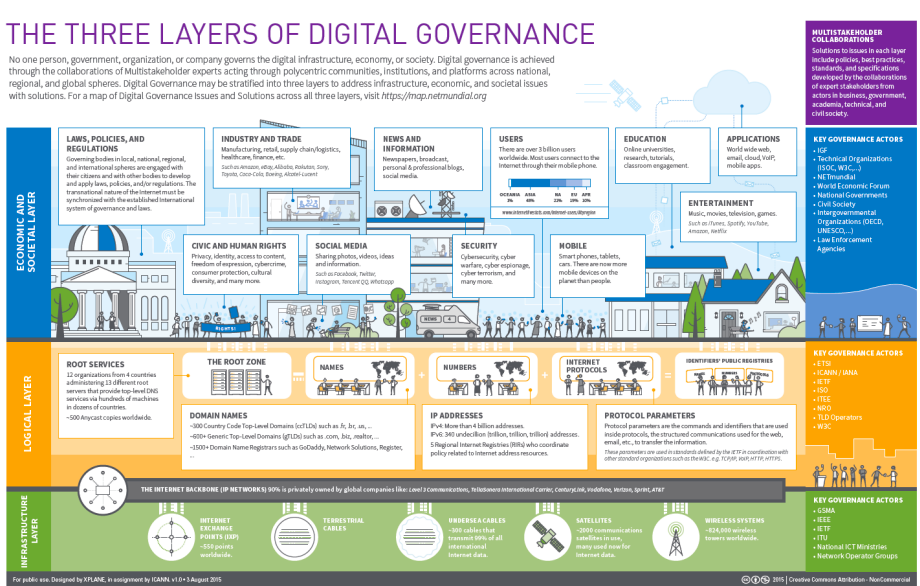
The Distributors of Internet Protocol Resources, Layer 3
Layer 3 (A function of the DNS layer) manages and distributes (allocates) IP resources to the ISP & Network Providers of Internet Protocol Resources, last mile, Layer 5, who in turn can be customers, owners, resellers, or the Users of Internet Protocols Resources, Layer 6 themselves. The Distributors of Internet Protocol Resources, Layer 3 are managed by the Numbers Resource Organization (NRO), the coordinating body/mechanism of the five (5) Regional Internet Registrars (RIR) who oversee and manage the allocation and registration of IP Addresses and ASN address space for their region. SEE NRO REGIONAL INTERNET REGISTRIES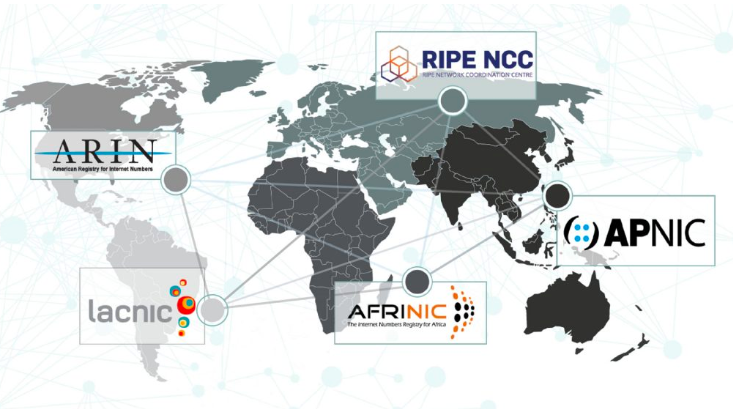
The Routing/Pathway Providers of Internet Protocol Resources, Layer 4
Layer 4 consist primarily of Tier1, Tier 2 & some Tier 3 ISPs, Telco pathway/routing providers and Autonomous Systems (AS). These pathway/routing providers are companies that own, operate, and sell access to the internet’s backbone infrastructure and services.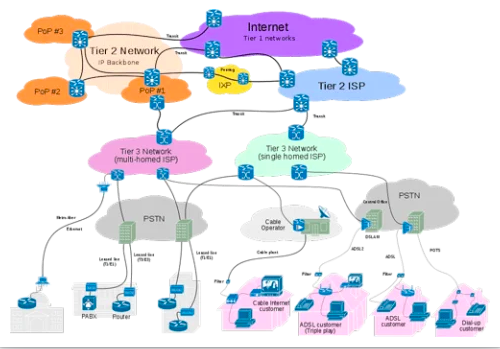 See World Economic Forum Cybercrime Prevention Principles for Internet Service Providers. Recommended Key principles: 1. Protect Consumers by default 2. Take action to raise awareness 3. Work more closely with manufactures 4. Take action to shore up the security of routing and signaling to defend against attacks.
See World Economic Forum Cybercrime Prevention Principles for Internet Service Providers. Recommended Key principles: 1. Protect Consumers by default 2. Take action to raise awareness 3. Work more closely with manufactures 4. Take action to shore up the security of routing and signaling to defend against attacks.
The ISP & Network Providers of Internet Protocol Resources, last mile, Layer 5
Layer 5 is primarily engaged in delivering Internet access to the Users of Internet Protocols Resources Layer 6 and focuses on local business and consumer market conditions(last mile service). They provide the "on-ramp" or local access to the Internet for the Users of Internet Protocols Resources, Layer 6, through cable, DSL, fiber, satellite or wireless access networks. Their coverage is limited to specific countries or sub regions, such as a metro area.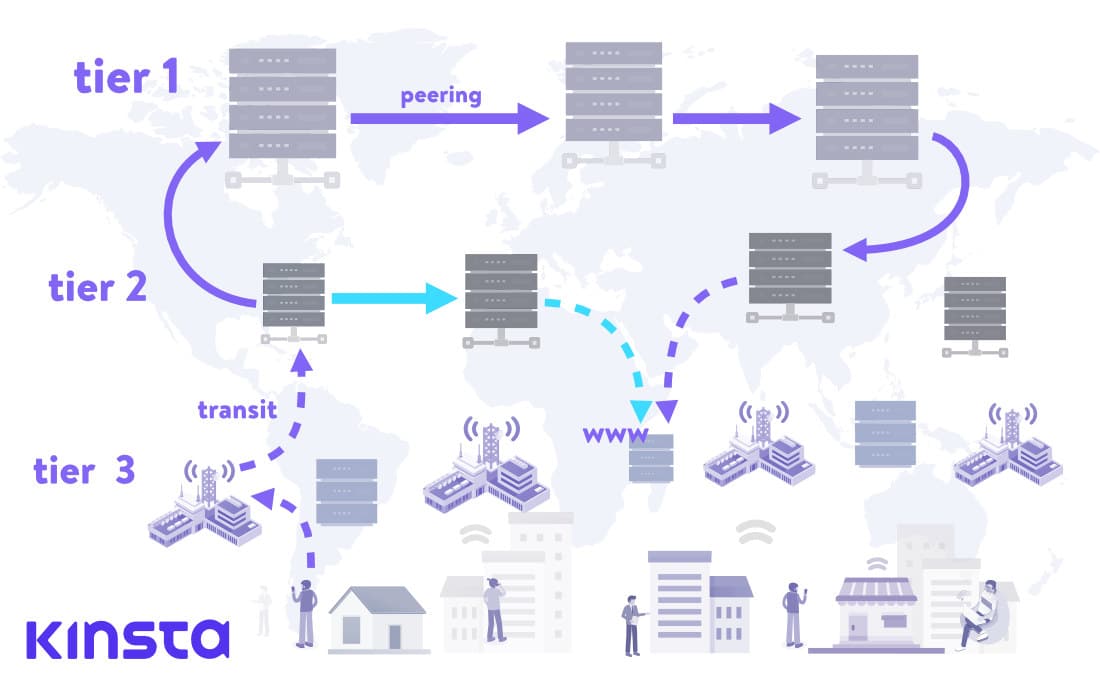
The Users of Internet Protocol Resources, Layer 6
Layer 6 is a focus on the Attack vector. There are Six Initial Access Attack Vectors (how the attacker gains initial access) for launching unauthorized access into your environment during a cyber-attack. They are a Browser, Link, Attachment (file, program or code), Insider, Scanning and Reconnaissance Exploitation (a triad) and Social Engineering, with each Initial Access Attack Vector being foundational to the beginning stages of every cyber-attack. Together or separately these Six Initial Access Attack Vectors serve as the opening segment of the attack pathway that every the Abusers of Internet Protocol Resources, Layer 7 will utilize as entry to the attack surface. Download Brochure
Download Brochure
The Abusers of Internet Protocol Resources, Layer 7
Layer 7 focuses of the Adversary, they are described as: Cyber-Criminal - An individual who commits cybercrimes, where he/she makes use of the computer either as a tool or as a target or as both. Hacktivist- The use of computer-based techniques such as hacking as a form of civil disobedience to promote a political agenda, ideological motives or social change. Competitors - Industry competitor, a competing interest involving cyber spying or espionage. An attempt to gain an economic advantage, targeting sensitive Intellectual Property. Insider (knowingly or unwitting) Threat to an organization that comes from people within the Organization, such as employees, former employees, contractors or business associates, anyone who has legitimate access, either by accidental or deliberate misuse. Nation State - Motivated by nationalism and tasked with gaining secrets from or disrupting other nations via cyber means. Organized crime entity employed by a national government.The Defenders of Internet Protocol Resources, Layer 8
In Layer 8 the defenders are described as: Government/Intelligence: They focus on Geo-political impact to policy. •Law enforcement: Prosecution in silos, interested in finding out who was behind the attack and being able to present enough evidence to support the attribution to a crime. •Cyber Security firms: Cybersecurity companies earn money by offering any number of services to clients, including providing outsourced technology support.•Private sector/Businesses: Profit driven, bottom line, return on investment •CERTS and CSIRTS: A computer emergency response team or computer security incident response team, is a historic term for an expert group that handles computer security incidents.•Defensive Researchers/Academia: Researchers conduct research in the technologies and techniques of cyber security which secures information systems of tomorrow.•Non-government Organization: Cybersecurity in Non-Profit and Non-Governmental Organizations are think-tanks of cyber security and policy experts with the vision of pioneering Cyber Peace Initiatives to build collective resiliency against cybercrimes & global threats of cyber warfare.•General Public: The goal of the general public is to practice safe security hygiene, learn and understand safe internet practices.The Countermeasures of Internet Protocol Resources, Layer 9A
The Countermeasures used to secure Internet Protocol Resources are described as (Source NIST) protective measures prescribed to meet the security objectives (i.e., confidentiality, integrity, and availability) specified for an information system. Safeguards may include security features, management controls, personnel security, and security of physical structures, areas, and devices. 1. Technology - Security Products 2. People - Security Services 3. Process – Security compliance, regulation, and requirements. See: Nonprofit Cyber is a coalition of implementation-focused cybersecurity nonprofits to collaborate, work together on projects, voluntarily align activities to minimize duplication and increase mutual support, and link the community to key stakeholders with a shared communication channel.
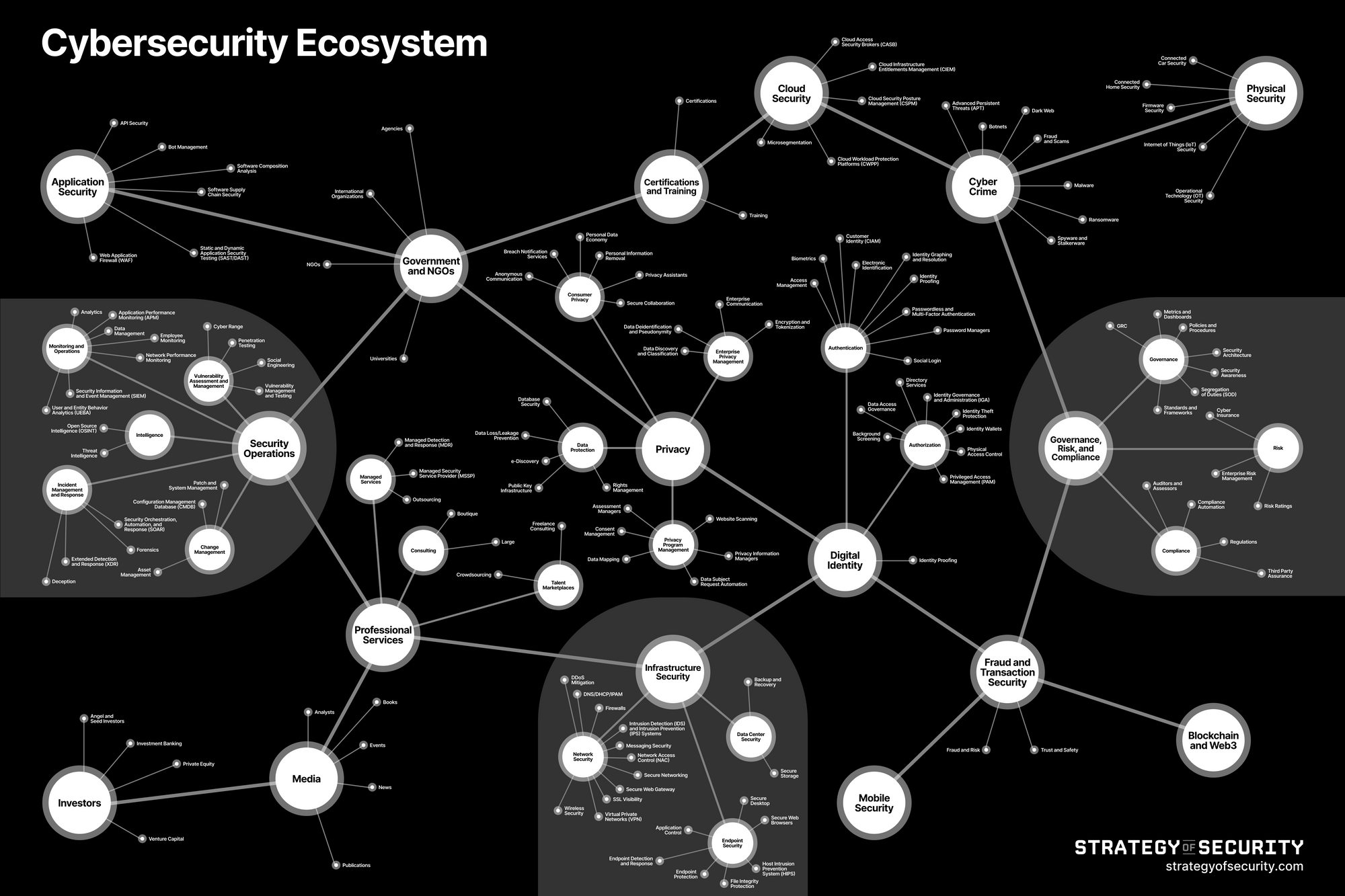
The Responders of Internet Protocol Resources, Layer 9B
The Responders Explained: The following (3) three steps are extremely important to responding to every cyber event: Step#1. Getting the right people involved and coordinating your efforts is key to any successful response. Step #2. Containing the problem while investigating the incident: (Containment Mode) A data breach contains three (3) basic components 1. How did they get in? (Has your system been accessed or is it infected modified)? 2. How did they move through your network and what did they take or alter? (move, change or alter) 3. How did they exit your system? Step #3. Collecting and reporting the factsThe Security vs Privacy of Internet Protocol Resources, Layer 10
Security and Privacy are both interlinked terms that are often used in conjunction with each other, while one cannot exist without the other, they are often misused. Privacy relates to any rights you have to control your personal information and how it’s used. Privacy is having the ability to protect sensitive information about personally identifiable information, while protection is really a security component. Others define it as the right to be left alone. Security on the other hand, refers to how your personal information is protected. As a society and as consumers we care about controlling who has our information, and we try to make sure those trusted do the right thing with it, in this context, there is little difference between Privacy and Security.